2020. 2. 11. 17:21ㆍ카테고리 없음
Author:Rudolf SteinerISBN:Genre:Body, Mind & SpiritFile Size:58.34 MBFormat:PDF, MobiDownload:982Read:257'As a general rule, wherever one finds alchemy in the West upon a Christian basis, the true Rose Cross is not distant. From this point of view, Rudolf Steiner's anthroposophy, to the extent that it is Rosicrucian, is alchemical. Alchemy, in this sense, is. The 'resurrection' of matter.'
- Christopher Bamford During the early seventeenth century, Europe was suddenly embroiled in controversy after the publication of the first Rosicrucian texts. Ever since, Rosicrucianism has been at the center of Western Christian esotericism. Forced underground by the Thirty Years War, it was secretly handed down by alchemists, hermeticists, and Masons to the nineteenth century, when it inspired new spiritual movements such as Theosophy, the Order of Golden Dawn, and Rudolf Steiner's spiritual science. The Secret Stream collects all of Steiner's discussions of the Rosicrucians, answering questions such as Who are the Rosicrucians?
What is Alchemy? What is the Rosicrucian path? What is the difference between Rosicrucianism and mysticism? And what does it mean for today?
The topics include the Tao and the Rose Cross; the history and mission of Christian Rosenkreutz; the nature of Rosicrucian practice and experience; the meaning of The Chymical Wedding, and Goethe's Rosicrucian poem 'The Mysteries.' Rosicrucian meditation is also discussed, including how to meditate on the Rose Cross itself. This important collection goes to the spiritual heart of anthroposophy, the essence of which is the Rosicrucian path. Edited and introduced by Christopher Bamford, The Secret Stream brings to light the hidden fraternity that has lived and worked since the fourtheenth century. It reveals the Rosicrucian path that is Christian, alchemical, and profoundly modern.
Author:John Brown MacleanISBN:Genre:HistoryFile Size:37.69 MBFormat:PDF, KindleDownload:750Read:299This work has been selected by scholars as being culturally important, and is part of the knowledge base of civilization as we know it. This work was reproduced from the original artifact, and remains as true to the original work as possible. Therefore, you will see the original copyright references, library stamps (as most of these works have been housed in our most important libraries around the world), and other notations in the work. This work is in the public domain in the United States of America, and possibly other nations.
Within the United States, you may freely copy and distribute this work, as no entity (individual or corporate) has a copyright on the body of the work. As a reproduction of a historical artifact, this work may contain missing or blurred pages, poor pictures, errant marks, etc. Scholars believe, and we concur, that this work is important enough to be preserved, reproduced, and made generally available to the public.
We appreciate your support of the preservation process, and thank you for being an important part of keeping this knowledge alive and relevant. Author:Lin LipetzISBN:702Genre:Body, Mind & SpiritFile Size:21.8 MBFormat:PDF, MobiDownload:608Read:249The Secret of Inner Presence begins with author Lin Lipetzs story of her spontaneous spiritual awakening in 1986. This amazing and unexpected event created an immediate awareness of a loving Inner Presence within her heart and a connection to another higher level of peace, contentment, and greater knowledge. She now knows that Inner Presence waits patiently to manifest within each person, and much of The Secret of Inner Presence is about providing the keys to bring about that shift in consciousness. As each of the eleven keys is practiced and experienced, the transformation toward a more complete understanding of the core-self will gradually evolve through the loving guidance of the conscious Universe. One of the eleven keys opens the way to intuitively listen to the many voices that will assist in this transformation through healing, new insights, dreams, problem solving, and caring advice.
Another key opens the way to deepen intuitively to the level of receiving messages from the Universe and possibly finding the guides that have been available since birth. This process is called Stream of Consciousness writing, and the powerful dialogues and inspirational poems the author has received in this way for many years are found in each chapter. Chapter by chapter, each of the eleven keys is presented, by both the spiritual Universe and the author, to help guide the reader to a higher dimension of the self. Author:Goutam PaulISBN:373Genre:ComputersFile Size:72.8 MBFormat:PDF, ePub, MobiDownload:778Read:1109RC4 Stream Cipher and Its Variants is the first book to fully cover the popular software stream cipher RC4.
With extensive expertise in stream cipher cryptanalysis and RC4 research, the authors focus on the analysis and design issues of RC4. They also explore variants of RC4 and the eSTREAM finalist HC-128. After an introduction to the vast field of cryptology, the book reviews hardware and software stream ciphers and describes RC4. It presents a theoretical analysis of RC4 KSA, discussing biases of the permutation bytes toward secret key bytes and absolute values. The text explains how to reconstruct the secret key from known state information and analyzes the RC4 PRGA in detail, including a sketch of state recovery attacks. The book then describes three popular attacks on RC4: distinguishing attacks, Wired Equivalent Privacy (WEP) protocol attacks, and fault attacks.
The authors also compare the advantages and disadvantages of several variants of RC4 and examine stream cipher HC-128, which is the next level of evolution after RC4 in the software stream cipher paradigm. The final chapter emphasizes the safe use of RC4. With open research problems in each chapter, this book offers a complete account of the most current research on RC4.
Author:Paul HutchinsISBN:338Genre:ReligionFile Size:39.84 MBFormat:PDF, ePub, MobiDownload:776Read:345A pictorial drama of the creation of Heaven and Earth based upon the awe-inspiring photo images from the Hubble and Spitzer space telescopes. Author, Paul Hutchins uncovers a grand drama on a universal scale that has been playing out since the invention of the telescope. He poses the question, is this grand drama merely in response to an ancient invitation recorded in the Book of Isaiah? It states in Isaiah 40:26, 'Look up into the heavens.' ' Who created all the stars? Through the use of his imagination and the invention of the telescope, man has discovered a once secret doorway to a world beyond imagination.
He has now, in this age of cutting edge technology developed flying space telescopes in his quest to know, how did we get here? What he has found has astounded him. Hutchins farther poses the question; if it took over 400 years of man’s imagination from when the telescope was invented, and countless other inventions including the Hubble and Spitzer space telescopes, to merely take photo images of the universe, then who’s imagination is responsible for the reality those photo images represent? As we peer through this doorway to the heavens and look upon these heavenly cosmic bodies, we find ourselves awed by their grandeur. The pressing question becomes too large to ignore.
Who is responsible for all these things? Could it be that we are now peering into the mind of a supreme architect with an imagination far beyond that of mere mortals? Could we be peering into the mind of imagination supreme? Could it be that we have been brought to this point in history unbeknownst to ourselves and given this technology by the one who extended that ancient invitation recorded by Isaiah 2700 years ago? Author:Ranjit LalISBN:612Genre:Juvenile FictionFile Size:63.95 MBFormat:PDF, ePubDownload:881Read:292She’s beautiful.
She’s fearless. She’s bewitching. So why is she the ‘leper’ of Pahadpur? Seventeen-year-old Sandeep and his younger brother, Manish, are not looking forward to spending three months in the remote Internet-challenged hill station of Pahadpur with their military-minded aunt. Apart from taking care of their kid sister, Chubs, who tends to wander off on her own, the boys have absolutely nothing to do in the holidays.
But there is more to Pahadpur than meets the eye. Sandeep and Manish discover that the family next door, at Falcon Heights, is shunned by all the townsfolk. Who is the mysterious girl who lives there and fl ies a falcon every morning? As they unravel the secret with their new friend Parul, two terrible but equally plausible stories emerge—only one of which can be true. When the truth is revealed, it brings all of them face-to-face with a horrifying fate, and it is left to little Chubs to save the day. Author:Rana BaruaISBN:677Genre:Business & EconomicsFile Size:40.10 MBFormat:PDF, ePub, DocsDownload:462Read:492This book constitutes the refereed proceedings of the 7th International Conference on Cryptology in India, INDOCRYPT 2006, held in Kolkata, India in December 2006. The 29 revised full papers presented together with 2 invited papers were carefully reviewed and selected from 186 submissions.
The papers are organized in topical sections on symmetric cryptography: attacks, hash functions, provable security: key agreement, provable security: public key cryptograpy, symmetric cryptography: design, modes of operation and message authentication codes, fast implementation of public key cryptography, id-based cryptography, as well as embedded systems and side channel attacks.
This article is about the stream cipher. For other uses, see.
RC4 GeneralDesignersFirst publishedLeaked in 1994(designed in 1987)Cipher detail40– 0000 bitsState size0000 bits ( 0000 effective)Rounds1Speed7 cycles per byte onModified Alleged RC4 on Intel Core 2: 13.9 cycles per byteIn, RC4 (Rivest Cipher 4 also known as ARC4 or ARCFOUR meaning Alleged RC4, see below) is a. While remarkable for its simplicity and speed in software, multiple vulnerabilities have been discovered in RC4, rendering it insecure. It is especially vulnerable when the beginning of the output is not discarded, or when nonrandom or related keys are used. Particularly problematic uses of RC4 have led to very insecure such as.As of 2015, there is speculation that some state cryptologic agencies may possess the capability to break RC4 when used in the. Has published to prohibit the use of RC4 in TLS; and have issued similar recommendations.In 2014, Ronald Rivest gave a talk and published a paper on an updated redesign called. A hardware accelerator of Spritz was published in Secrypt, 2016.
The authors have shown that due to multiple nested calls required to produce output bytes, Spritz performs rather slowly compared to other hash functions such as SHA-3 and best known hardware implementation of RC4. HistoryRC4 was designed by of in 1987. While it is officially termed 'Rivest Cipher 4', the RC acronym is alternatively understood to stand for 'Ron's Code' (see also, and ).RC4 was initially a, but in September 1994 a description of it was anonymously posted to the mailing list.
It was soon posted on the, and from there to many sites on the Internet. The leaked code was confirmed to be genuine as its output was found to match that of proprietary software using licensed RC4.
Because the algorithm is known, it is no longer a trade secret. The name RC4 is trademarked, so RC4 is often referred to as ARCFOUR or ARC4 (meaning alleged RC4) to avoid trademark problems. Has never officially released the algorithm; Rivest has, however, linked to the article on RC4 in his own course notes in 2008 and confirmed the history of RC4 and its code in a 2014 paper by him.RC4 became part of some commonly used encryption protocols and standards, such as in 1997 and in 2003/2004 for wireless cards; and in 1995 and its successor in 1999, until it was prohibited for all versions of TLS by in 2015, due to the weakening or breaking RC4 used in SSL/TLS. The main factors in RC4's success over such a wide range of applications have been its speed and simplicity: efficient implementations in both software and hardware were very easy to develop.
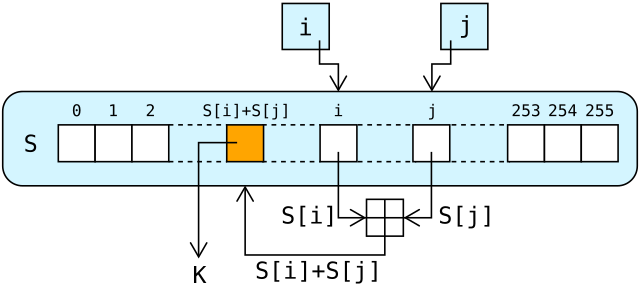
DescriptionRC4 generates a (a ). As with any stream cipher, these can be used for encryption by combining it with the plaintext using bit-wise; decryption is performed the same way (since exclusive-or with given data is an ). (This is similar to the except that generated pseudorandom bits, rather than a prepared stream, are used.) To generate the keystream, the cipher makes use of a secret internal state which consists of two parts:. A of all 256 possible (denoted 'S' below).
Two 8-bit index-pointers (denoted 'i' and 'j').The permutation is initialized with a variable length, typically between 40 and 2048 bits, using the algorithm (KSA). Once this has been completed, the stream of bits is generated using the pseudo-random generation algorithm (PRGA). Key-scheduling algorithm (KSA)The algorithm is used to initialize the permutation in the array 'S'. 'keylength' is defined as the number of bytes in the key and can be in the range 1 ≤ keylength ≤ 256, typically between 5 and 16, corresponding to a of 40 – 128 bits. First, the array 'S' is initialized to the.
S is then processed for 256 iterations in a similar way to the main PRGA, but also mixes in bytes of the key at the same time. For i from 0 to 255Si:= iendforj:= 0for i from 0 to 255j:= (j + Si + keyi keylength) mod 256swap values of Si and Sjendfor Pseudo-random generation algorithm (PRGA).
The lookup stage of RC4. The output byte is selected by looking up the values of Si and Sj, adding them together modulo 256, and then using the sum as an index into S; S(Si + Sj) is used as a byte of the key stream, K.For as many iterations as are needed, the PRGA modifies the state and outputs a byte of the keystream. In each iteration, the PRGA increments i, looks up the ith element of S, S i, and adds that to j, exchanges the values of S i and S j, and then uses the sum S i + S j (modulo 256) as an index to fetch a third element of S, (the keystream value K below) which is bitwise exclusive OR'ed ('ed) with the next byte of the message to produce the next byte of either ciphertext or plaintext. Each element of S is swapped with another element at least once every 256 iterations.
I:= 0j:= 0while GeneratingOutput:i:= (i + 1) mod 256j:= (j + Si) mod 256of Si and SjK:= S(Si + Sj) mod 256output Kendwhile RC4-based random number generatorsSeveral include arc4random, an API originating in providing access to a random number generator originally based on RC4. In OpenBSD 5.5, released in May 2014, arc4random was modified to use. As of January 2015, the implementation of arc4random in also uses ChaCha20, however, the implementations of arc4random in, 's libbsd, and are still based on RC4.Proposed new random number generators are often compared to the RC4 random number generator.Several attacks on RC4 are able to. ImplementationMany stream ciphers are based on (LFSRs), which, while efficient in hardware, are less so in software. The design of RC4 avoids the use of LFSRs, and is ideal for software implementation, as it requires only byte manipulations. It uses 256 bytes of memory for the state array, S0 through S255, k bytes of memory for the key, key0 through keyk-1, and integer variables, i, j, and K.
Rc4 Stream Cipher And Its Variants Pdf To Word Converter
Performing a modular reduction of some value modulo 256 can be done with a with 255 (which is equivalent to taking the low-order byte of the value in question). SecurityUnlike a modern stream cipher (such as those in ), RC4 does not take a separate alongside the key. This means that if a single long-term key is to be used to securely encrypt multiple streams, the protocol must specify how to combine the nonce and the long-term key to generate the stream key for RC4. One approach to addressing this is to generate a 'fresh' RC4 key by a long-term key with a. However, many applications that use RC4 simply concatenate key and nonce; RC4's weak then gives rise to, like the (which is famous for breaking the standard).Because RC4 is a, it is more than common.
If not used together with a strong (MAC), then encryption is vulnerable to a. The cipher is also vulnerable to a if not implemented correctly. Furthermore, inadvertent double encryption of a message with the same key may accidentally output plaintext rather than ciphertext because the nature of the XOR function would result in the second operation reversing the first.It is noteworthy, however, that RC4, being a stream cipher, was for a period of time the only common cipher that was immune to the 2011 on.
The attack exploits a known weakness in the way is used with all of the other ciphers supported by TLS 1.0, which are all block ciphers.In March 2013, there were new attack scenarios proposed by Isobe, Ohigashi, Watanabe and Morii, as well as AlFardan, Bernstein, Paterson, Poettering and Schuldt that use new statistical biases in RC4 key table to recover plaintext with large number of TLS encryptions.The use of RC4 in TLS is prohibited by published in February 2015. Roos's biases and key reconstruction from permutationIn 1995, Andrew Roos experimentally observed that the first byte of the keystream is correlated to the first three bytes of the key and the first few bytes of the permutation after the KSA are correlated to some linear combination of the key bytes. These biases remained unexplained until 2007, when Goutam Paul, Siddheshwar Rathi and Subhamoy Maitra proved the keystream-key correlation and in another work Goutam Paul and Subhamoy Maitra proved the permutation-key correlations.
The latter work also used the permutation-key correlations to design the first algorithm for complete key reconstruction from the final permutation after the KSA, without any assumption on the key. This algorithm has a constant probability of success in a time which is the square root of the exhaustive key search complexity. Subsequently, many other works have been performed on key reconstruction from RC4 internal states. Subhamoy Maitra and Goutam Paul also showed that the Roos type biases still persist even when one considers nested permutation indices, like SSi or SSSi. These types of biases are used in some of the later key reconstruction methods for increasing the success probability. Biased outputs of the RC4The keystream generated by the RC4 is biased in varying degrees towards certain sequences making it vulnerable to.
The best such attack is due to Itsik Mantin and who showed that the second output byte of the cipher was biased toward zero with probability 1/128 (instead of 1/256). This is due to the fact that if the third byte of the original state is zero, and the second byte is not equal to 2, then the second output byte is always zero. Such bias can be detected by observing only 256 bytes.and of showed that the first and the second bytes of the RC4 were also biased. The number of required samples to detect this bias is 2 25 bytes.Scott Fluhrer and David McGrew also showed such attacks which distinguished the keystream of the RC4 from a random stream given a gigabyte of output.The complete characterization of a single step of RC4 PRGA was performed by Riddhipratim Basu, Shirshendu Ganguly, Subhamoy Maitra, and Goutam Paul. Considering all the permutations, they prove that the distribution of the output is not uniform given i and j, and as a consequence, information about j is always leaked into the output. Fluhrer, Mantin and Shamir attack. Main article:In 2001, a new and surprising discovery was made by Fluhrer, Mantin and: over all possible RC4 keys, the statistics for the first few bytes of output keystream are strongly non-random, leaking information about the key.
If the nonce and long-term key are simply concatenated to generate the RC4 key, this long-term key can be discovered by analysing a large number of messages encrypted with this key. This and related effects were then used to break the ('wired equivalent privacy') encryption used with. This caused a scramble for a standards-based replacement for WEP in the 802.11 market, and led to the effort and.Protocols can defend against this attack by discarding the initial portion of the keystream. Such a modified algorithm is traditionally called 'RC4-dropn', where n is the number of initial keystream bytes that are dropped. The SCAN default is n = 768 bytes, but a conservative value would be n = 3072 bytes.The Fluhrer, Mantin and Shamir attack does not apply to RC4-based SSL, since SSL generates the encryption keys it uses for RC4 by hashing, meaning that different SSL sessions have unrelated keys. Klein's attackIn 2005, Andreas Klein presented an analysis of the RC4 stream cipher showing more correlations between the RC4 keystream and the key.
Erik Tews, Ralf-Philipp Weinmann, and Andrei Pychkine used this analysis to create aircrack-ptw, a tool which cracks 104-bit RC4 used in 128-bit WEP in under a minute. Whereas the Fluhrer, Mantin, and Shamir attack used around 10 million messages, aircrack-ptw can break 104-bit keys in 40,000 frames with 50% probability, or in 85,000 frames with 95% probability. Combinatorial problemA combinatorial problem related to the number of inputs and outputs of the RC4 cipher was first posed by Itsik Mantin and in 2001, whereby, of the total 256 elements in the typical state of RC4, if x number of elements ( x ≤ 256) are only known (all other elements can be assumed empty), then the maximum number of elements that can be produced deterministically is also x in the next 256 rounds.
This conjecture was put to rest in 2004 with a formal proof given. Royal Holloway attackIn 2013, a group of security researchers at the Information Security Group at Royal Holloway, University of London reported an attack that can become effective using only 2 24 encrypted messages. While yet not a practical attack for most purposes, this result is sufficiently close to one that it has led to speculation that it is plausible that some state cryptologic agencies may already have better attacks that render RC4 insecure. Given that as of 2013 a large amount of traffic uses RC4 to avoid recent attacks on block ciphers that use, if these hypothetical better attacks exist, then this would make the TLS-with-RC4 combination insecure against such attackers in a large number of practical scenarios.In March 2015 researcher to Royal Holloway announced improvements to their attack, providing a 2 26 attack against passwords encrypted with RC4, as used in TLS. Bar-mitzvah attack. Main article:On the Black Hat Asia 2015, Itsik Mantin presented another attack against SSL using RC4 cipher. NOMORE attackIn 2015, security researchers from presented new attacks against RC4 in both.
Dubbed the Numerous Occurrence MOnitoring & Recovery Exploit (NOMORE) attack, it is the first attack of its kind that was demonstrated in practice. Their attack against can decrypt a secure within 75 hours.
The attack against WPA-TKIP can be completed within an hour, and allows an attacker to decrypt and inject arbitrary packets. RC4 variantsAs mentioned above, the most important weakness of RC4 comes from the insufficient key schedule; the first bytes of output reveal information about the key. This can be corrected by simply discarding some initial portion of the output stream. This is known as RC4-drop N, where N is typically a multiple of 256, such as 768 or 1024.A number of attempts have been made to strengthen RC4, notably Spritz, RC4A, and RC4+. RC4Aand have proposed an RC4 variant, which they call RC4A.RC4A uses two state arrays S1 and S2, and two indexes j1 and j2.
Main article:Variably Modified Permutation Composition (VMPC) is another RC4 variant. It uses similar key schedule as RC4, withj:= S(j + Si + keyi mod keylength) mod 256 iterating 3 x 256 = 768 times rather than 256, and with an optional additional 768 iterations to incorporate an initial vector. The output generation function operates as follows: All arithmetic is performed modulo 256.i:= 0while GeneratingOutput:a:= Sij:= Sj + aoutput SSSj + 1Swap Si and Sj ( b:= Sj; Si:= b; Sj:= a))i:= i + 1endwhileThis was attacked in the same papers as RC4A, and can be distinguished within 2 38 output bytes. RC4 +RC4 + is a modified version of RC4 with a more complex three-phase key schedule (taking about 3× as long as RC4, or the same as RC4-drop512), and a more complex output function which performs four additional lookups in the S array for each byte output, taking approximately 1.7× as long as basic RC4. All arithmetic modulo 256. are left and right shift, ⊕ is exclusive OR while GeneratingOutput:i:= i + 1a:= Sij:= j + aSwap Si and Sj ( b:= Sj; Si:= b; Sj:= a)c:= Si3 + Sj3output (Sa+b + Sc⊕0xAA) ⊕ Sj+bendwhileThis algorithm has not been analyzed significantly.
SpritzRon Rivest and Jacob Schuldt have proposed replacing RC4 with an improved and slightly modified version dubbed Spritz: All arithmetic is performed modulo 256 while GeneratingOutput:i:= i + wj:= k + Sj + Sik:= k + i + Sjswap values of Si and Sjoutput z:= Sj + Si + Sz + kendwhileThe value w, is to the size of the S array. So after 256 iterations of this inner loop, the value i (incremented by w every iteration) has taken on all possible values 0.255, and every byte in the S array has been swapped at least once.Like other, Spritz can be used to build a cryptographic hash function, a deterministic random bit generator , an encryption algorithm that supports with associated data (AEAD), etc.Spritz was broken by Banik and Isobe. Prasithsangaree & P. Krishnamurthy (2003). Archived from (PDF) on 3 December 2013.
Retrieved 22 September 2015. Andrei Popov (February 2015). RFC 7465. Lucian Constantin (14 May 2014). ComputerWorld. J. Lindell (2014), Introduction to Modern Cryptography, Chapman and Hall/CRC, p.
77. John Leyden (6 September 2013). The Register. Retrieved 2015-01-03.
12 November 2013. Retrieved 2013-12-04. Rivest, Ron; Schuldt, Jacob (27 October 2014). Retrieved 26 October 2014.
Debjyoti Bhattacharjee and Anupam Chattopadhyay. Secrypt 2016. Retrieved 29 July 2016. (Mailing list). 9 September 1994.
Archived from on 22 July 2001. Retrieved 2007-05-28.
Retrieved 23 June 2014. Retrieved 21 September 2014., ed. (21 July 2014). BSD Cross Reference, OpenBSD src/lib/. Retrieved 2015-01-13. ChaCha based random number generator for OpenBSD. riastradh, ed.
(16 November 2014). BSD Cross Reference, NetBSD src/lib/. Retrieved 2015-01-13. Legacy arc4random(3) API from OpenBSD reimplemented using the ChaCha20 PRF, with per-thread state. Retrieved 6 January 2015.
Retrieved 6 January 2015. Retrieved 6 January 2015. Retrieved 6 January 2015. Bartosz Zoltak.2010?. Chefranov, A.G.2006.
Itsik Mantin, (2001). (PDF): 152 – 164. CS1 maint: Uses authors parameter (link). RSA Laboratories. 1 September 2001. Sklyarov, Dmitry (2004). A-List Publishing.
92–93. Isobe, Takanori; Ohigashi, Toshihiro (10–13 Mar 2013).
Hiroshima University. Retrieved 2014-10-27. Pouyan Sepehrdad; Serge Vaudenay; Martin Vuagnoux (2011). Lecture Notes in Computer Science. 6544: 74–91. Green, Matthew. Cryptography Engineering.
Retrieved 12 March 2013. Nadhem AlFardan, Dan Bernstein, Kenny Paterson, Bertram Poettering and Jacob Schuldt.
Royal Holloway University of London. Retrieved 13 March 2013.
CS1 maint: Multiple names: authors list (link). Andrew Roos.
A Class of Weak Keys in the RC4 Stream Cipher. Two posts in sci.crypt, message-id 43u1eh$1j3@hermes.is.co.za and 44ebge$llf@hermes.is.co.za, 1995.

Goutam Paul, Siddheshwar Rathi and Subhamoy Maitra. On Non-negligible Bias of the First Output Byte of RC4 towards the First Three Bytes of the Secret Key. Proceedings of the International Workshop on Coding and Cryptography (WCC) 2007, pages 285–294 and Designs, Codes and Cryptography Journal, pages 123–134, vol. 1-3, December 2008. Goutam Paul and Subhamoy Maitra. Permutation after RC4 Key Scheduling Reveals the Secret Key.
SAC 2007, pages 360–377, vol. 4876, Springer.
Eli Biham and Yaniv Carmeli. Efficient Reconstruction of RC4 Keys from Internal States.
FSE 2008, pages 270–288, vol. 5086, Lecture Notes in Computer Science, Springer. Mete Akgun, Pinar Kavak, Huseyin Demirci. New Results on the Key Scheduling Algorithm of RC4. INDOCRYPT 2008, pages 40–52, vol. 5365, Lecture Notes in Computer Science, Springer.
Riddhipratim Basu, Subhamoy Maitra, Goutam Paul and Tanmoy Talukdar. On Some Sequences of the Secret Pseudo-random Index j in RC4 Key Scheduling. Proceedings of the 18th International Symposium on Applied Algebra, Algebraic Algorithms and Error Correcting Codes (AAECC), 8–12 June 2009, Tarragona, Spain, pages 137–148, vol. 5527, Lecture Notes in Computer Science, Springer. Subhamoy Maitra and Goutam Paul.
New Form of Permutation Bias and Secret Key Leakage in Keystream Bytes of RC4. Proceedings of the 15th Fast Software Encryption (FSE) Workshop, 10–13 February 2008, Lausanne, Switzerland, pages 253–269, vol. 5086, Lecture Notes in Computer Science, Springer.,. (PDF): 52 – 67. CS1 maint: Uses authors parameter (link). Scott R. Fluhrer, David A.
(PDF): 19 – 30. CS1 maint: Uses authors parameter (link). Basu, Riddhipratim; Ganguly, Shirshendu; Maitra, Subhamoy; Paul, Goutam (2008). 'A Complete Characterization of the Evolution of RC4 Pseudo Random Generation Algorithm'. Journal of Mathematical Cryptology.
2 (3): 257–289. Scott R.
Fluhrer, Itsik Mantin and Adi Shamir, Weaknesses in the Key Scheduling Algorithm of RC4. 2001, pp1 – 24. in the 'Standard Cryptographic Algorithm Naming' database.
Ron Rivest. A. Klein, Attacks on the RC4 stream cipher, Designs, Codes and Cryptography (2008) 48:269–286. Erik Tews, Ralf-Philipp Weinmann, Andrei Pyshkin.
and, A New Weakness in the RC4 Keystream Generator and an Approach to Improve the Security of the Cipher. – FSE 2004, pp245 – 259. John Leyden (15 March 2013). The Register.
AlFardan; et al. (8 July 2013). Information Security Group, Royal Holloway, University of London. Information Security Group, Royal Holloway, University of London. Retrieved 2013-09-06. Retrieved November 19, 2016. (PDF).
Retrieved November 19, 2016. Mathy Vanhoef and Frank Piessens (9 August 2015). CS1 maint: Uses authors parameter (link). Ilya Mironov (1 June 2002), Advances in Cryptology – CRYPTO 2002, Lecture Notes in Computer Science, 2442, Springer-Verlag, pp. 304–319,:, 3-540-44050-X, Cryptology ePrint Archive: Report 2002/067, retrieved 2011-11-04.; (2004), Fast Software Encryption, FSE 2004, Lecture Notes in Computer Science, 3017, Springer-Verlag, pp. 245–259,:, 3-540-22171-9, retrieved 2011-11-04.
Alexander Maximov (22 February 2007), Cryptology ePrint Archive: Report 2007/070, retrieved 2011-11-04. Yukiyasu Tsunoo; Teruo Saito; Hiroyasu Kubo; Maki Shigeri; Tomoyasu Suzaki; Takeshi Kawabata (2005), (PDF). Bartosz Zoltak (2004), (PDF), Fast Software Encryption, FSE 2004, Lecture Notes in Computer Science, 3017, Springer-Verlag, pp. 210–225,:, 3-540-22171-9, retrieved 2011-11-04.
Subhamoy Maitra; Goutam Paul (19 September 2008), Progress in Cryptology – INDOCRYPT 2008, Lecture Notes in Computer Science, 5365, Springer-Verlag, pp. 27–39,:, 3-540-89753-4, Cryptology ePrint Archive: Report 2008/396, retrieved 2011-11-04. Banik, Subhadeep; Isobe, Takanori (2016-03-20). Peyrin, Thomas, ed. Lecture Notes in Computer Science. Springer Berlin Heidelberg.
928. Hongjun Wu, 'The Misuse of RC4 in Microsoft Word and Excel'. Archived from on 11 July 2010. Retrieved 2010-07-08.Further reading. Paul, Goutam; Subhamoy Maitra (2011). 359. (1995).
'Chapter 17 – Other Stream Ciphers and Real Random-Sequence Generators'. 9094.External links.,. – Improved Arcfour Modes for the Secure Shell (SSH) Transport Layer Protocol. – Test Vectors for the Stream Cipher RC4. – Prohibiting RC4 Cipher Suites.RC4 in WEP.